Cryptography Terminology: Unlocking the Secrets of Secure Systems
Understanding cryptography is crucial in today's digital world. This guide demystifies key concepts, explaining them in clear, concise terms. Let's explore the building blocks of secure communication. Did you know that even seemingly simple actions, like sending an email, rely heavily on sophisticated cryptographic techniques?
Symmetric Encryption: One Key to Rule Them All
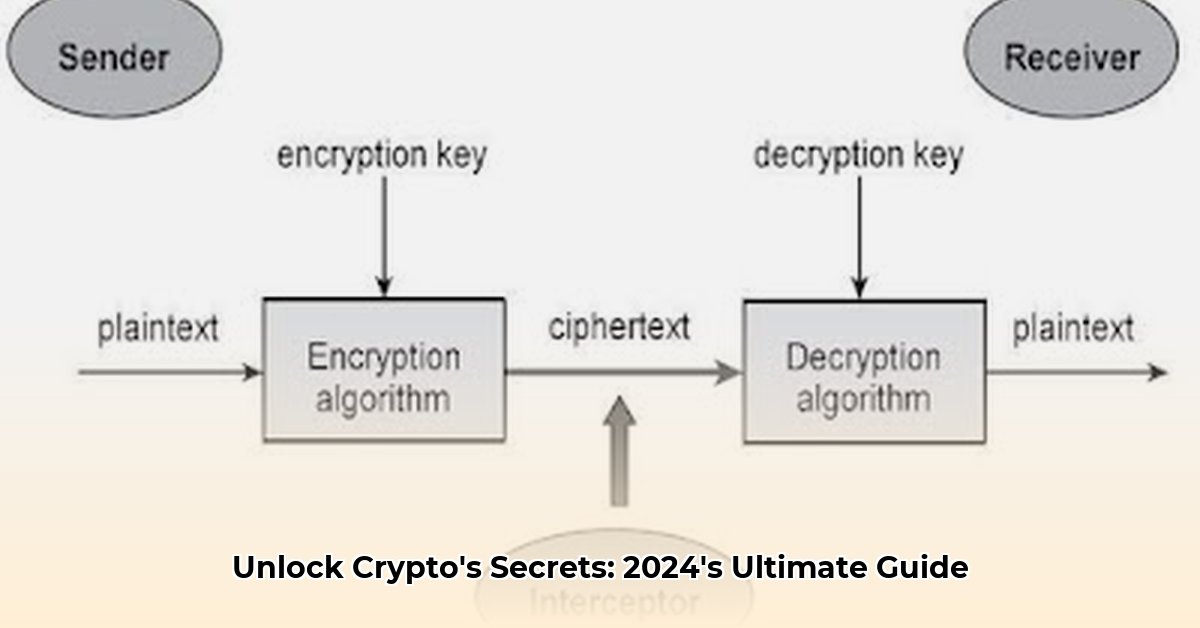
Symmetric encryption uses the same secret key to encrypt and decrypt data. It's like having a secret codebook – both sender and receiver need an identical copy. Popular algorithms include AES (Advanced Encryption Standard), known for its speed and efficiency in protecting large datasets. However, securely sharing this key presents a significant challenge. What are the implications of using the same key and how can we mitigate these?
Asymmetric Encryption: The Public and Private Key Dance
Asymmetric encryption employs a pair of keys: a public key for encryption, freely shared, and a private key for decryption, kept secret. This elegantly solves the key-exchange problem of symmetric encryption. Think of a mailbox: anyone can drop a letter in (public key), but only the owner has the key to open it (private key). RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) are prominent examples. While robust, asymmetric encryption is slower than symmetric encryption. How does this speed difference affect real-world applications?
Hashing: The Digital Fingerprint
Hashing generates a unique "fingerprint" (hash) for data. This process is one-way; you can't reverse the hash to get the original data. It's invaluable for verifying data integrity – any alteration changes the fingerprint. SHA-256 and SHA-3 are widely used hashing algorithms. What strategies exist for mitigating hash collisions, and how prevalent are they in practice?
Cryptographic Attacks: The Threats to Encryption
Cryptographic systems, while robust, face constant threats from various attacks. Brute-force attacks try every possible key, while side-channel attacks exploit system vulnerabilities during encryption/decryption. Social engineering, manipulating users to reveal secrets, remains a significant concern. The emergence of quantum computing introduces further complexity, potentially rendering current algorithms vulnerable. Dr. Anya Sharma, Chief Cryptographer at SecureTech Solutions, states: "Layered security is paramount. Multiple defensive mechanisms create a far stronger system than relying on a single approach."
Picking the Right Tool: Algorithm Selection
Choosing the right encryption algorithm depends on several factors: data sensitivity, required speed, and regulatory compliance. AES excels for speed and efficiency with large datasets. RSA is ideal for secure key exchange and digital signatures. ECC offers a balance of security and efficiency, particularly on resource-constrained devices. The choice involves careful consideration of speed versus key management security. What are the long-term implications of current encryption techniques in the face of powerful quantum computers?
| Algorithm Category | Example Algorithm | Advantages | Disadvantages |
|---|---|---|---|
| Symmetric Encryption | AES, 3DES | Very fast, efficient for large datasets | Secure key distribution is a critical challenge |
| Asymmetric Encryption | RSA, ECC | Secure key exchange, ideal for digital signatures | Much slower than symmetric encryption; computationally intensive |
| Hashing | SHA-256, SHA-3 | Verifies data integrity; detects tampering | Susceptible to collision attacks (though extremely improbable with modern algorithms) |
How to Choose the Best Encryption Algorithm for Sensitive Data Considering Quantum Computing Threats
Quantum computing poses a significant threat to current encryption standards. Algorithms previously considered secure are vulnerable to future quantum computer capabilities. This necessitates a shift towards post-quantum cryptography (PQC). How can organizations proactively prepare for this technological shift?
Understanding the Quantum Threat
Quantum computers utilize quantum mechanics to perform calculations far surpassing classical computers. Shor's algorithm can efficiently factor large numbers, undermining RSA encryption. Grover's algorithm accelerates brute-force attacks, posing a risk to symmetric algorithms like AES. This isn't a distant concern; quantum computing is rapidly advancing. Recent research shows a significant increase in the computational power of these systems.
Choosing the Right Algorithm: A Step-by-Step Guide
Assess Your Risk: Evaluate the sensitivity and longevity of confidentiality requirements for your data. Different levels of sensitivity will require different algorithms and strategies.
Consider the Timeline: Consider both immediate and long-term security needs. A phased approach often helps to manage risks effectively.
Explore Post-Quantum Cryptography (PQC): NIST is standardizing PQC algorithms, offering resistant alternatives. Research and select algorithms (e.g., CRYSTALS-Kyber, Dilithium) that align with your requirements and risk tolerance.
Implement Crypto-Agility: Design systems for easy algorithm changes, ensuring a smooth transition to newer algorithms as they become available. This helps to manage the risks of future technological advances.
Regularly Update and Monitor: Cryptography is a dynamic field. Continuously monitor for new threats and algorithm advancements, updating your security protocols proactively.
Algorithm Comparison: A Simplified Summary
| Algorithm Category | Example Algorithm(s) | Quantum Vulnerability | Strengths | Weaknesses |
|---|---|---|---|---|
| Symmetric | AES-256, ChaCha20 | Limited (Grover's) | Speed, efficiency | Key distribution complexity |
| Asymmetric | RSA, ECC | High (Shor's) | Key exchange, digital signatures | Relatively slower |
| Post-Quantum | CRYSTALS-Kyber, Dilithium | Theoretically resistant | Designed to withstand quantum computer attacks | Relatively new, undergoing further testing |
Note: This table offers a concise summary. The security of any algorithm depends significantly on its implementation and key management.
Key Takeaways:
- Prioritize layered security, employing multiple protective measures beyond encryption.
- Tailor encryption choices to your data's sensitivity and specific needs.
- Plan for future-proofing your systems with crypto-agility.
- Stay updated on quantum computing and cryptographic advancements.
- Consult cybersecurity experts for guidance on intricate matters.